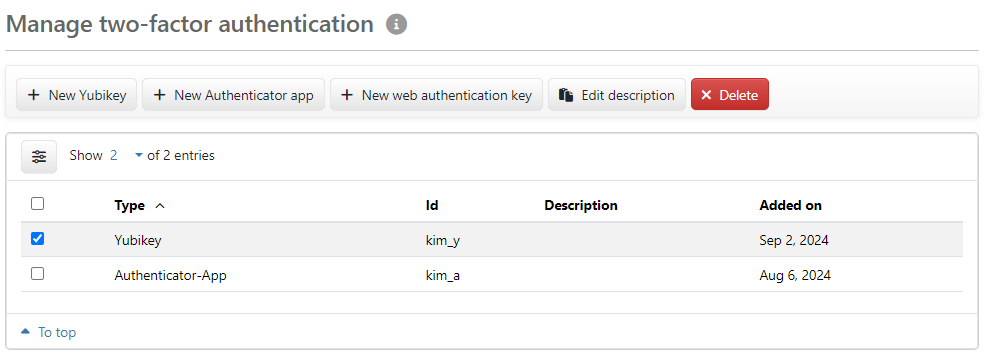
Figure: Managing the two-factor authentication
Each user can use two-factor authentication in addition to the password to increase security. On this page, you can configure one or more security keys, even several of the same type. As soon as a key exists, two-factor authentication is activated. From then on you will need the one-time password of one of these keys to log in to the program and to manage your security keys. By default, two-factor authentication is also used to sign orders and payments. You can switch off this use in your personal user preferences.
The overview shows which security keys you have set up. The key type and an ID (serial number, identifier, account or user name) are defined during configuration and cannot be changed.
If you want to use a hardware security key, you can choose between the following methods: Yubikey and Web authentication key. For the method Authenticator app, an app must be installed on a mobile device that is permanently available. Clicking on one of the buttons loads a page on which you can set up the respective key. BL Portal can be preconfigured so that only certain security keys are offered.
It is advisable to set up at least one additional security key as a backup in case a hardware device or authenticator app fails.
A description, max. 255 characters, is an optional entry which, for example, names the difference between equivalent security keys. The description can be entered during creation, added to later or changed. To edit, select a row and use the button to open a dialog box for entering the description. An administrator or manager can carry out this action on your behalf.
You can mark and delete security keys individually. This opens a page on which you must enter the one-time password of the key to be deleted or another key for confirmation. If you want to deactivate two-factor authentication, you must delete all the keys you have set up. An administrator or manager can carry out this action on your behalf.

Figure: Managing the two-factor authentication